At Pyramid Systems, innovation is more than just a buzzword, it’s a core philosophy that drives our approach to solving client challenges and fostering employee…
Read MoreAs Pyramid Systems marks three decades of delivering innovative IT solutions, we are proud to announce the appointment of David Chow as our new Chief…
Read MoreAt Pyramid Systems, we’re committed to supporting our team members as they navigate their career journeys and financial goals. That is why we are proud…
Read MoreThis summer, Pyramid Systems (Pyramid) encouraged employees to prioritize their health through the “Smiles for Miles” fitness challenge. Following the success of our January step…
Read MoreWe are thrilled to announce that Pyramid Systems has been awarded a prime contract by the U.S. Department of Agriculture (USDA) to provide operations, maintenance,…
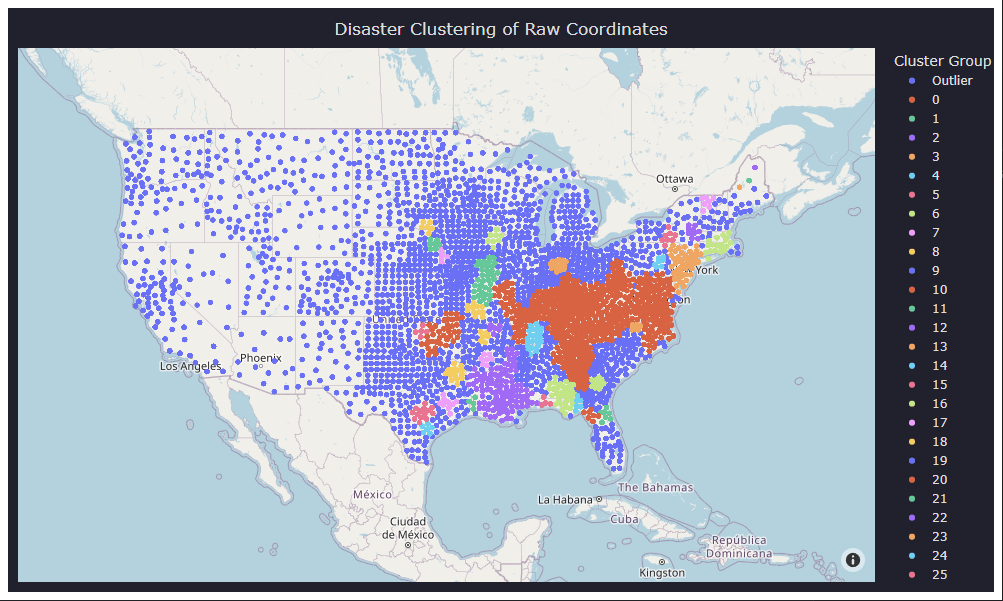
Read MoreEnhanced Government grant programs serve as catalysts for scientific breakthroughs, cutting-edge innovations, bolstering emergency response capabilities, fostering economic prosperity, and uplifting societal well-being. The hallmark…
Read MorePyramid Systems, Inc. (Pyramid) interns successfully developed an adaptable end-to-end data pipeline within the Google Cloud Platform (GCP), facilitating streamlined data processing for machine learning…
Read MorePyramid Systems is pleased to announce that we have been recertified as an AWS Advanced Tier Partner for 2024, a prestigious acknowledgment within the AWS…
Read MoreAt Pyramid Systems, we take immense pride in recognizing the invaluable contributions of every team member to our collective success. Understanding the core values of…
Read MoreBy: Owen Erhahon Discover the pitfalls of traditional test data creation and the risks they pose. Explore how synthetic data, powered by AI, offers a…
Read More